US financial institutions are being pounded with high-powered cyberattacks that some suspect are being orchestrated by Iran as payback for political sanctions.
“There is no doubt within the US government that Iran is behind these attacks,” James Lewis, a former official in the State and Commerce departments and now a computer security expert at the Center for Strategic and International Studies, told the New York Times.
While the identities of those behind the online onslaught officially remain a mystery, it was clear they were using a new weapon for slamming bank Web sites with overwhelming numbers or requests for information.
The attackers infected datacenters used to host services in the Internet “cloud” and commandeered massive computing power to back distributed denial of service (DDoS) attacks, according to security experts.
DDoS attacks have been a basic hacker weapon for quite some time, but they have typically involved armies of personal computers tainted with viruses and coordinated to make simultaneous requests at Web sites.
“They are essentially going from a pistol to a cannon,” Carl Herberger, Radware vice president of security solutions, said of cyberattackers using datacenters.
The top 20 US banks on Wednesday were being hit with a third wave of attacks, each of which has been preceded by a claim of responsibility by a group calling itself Izz ad-Din al-Qassam Cyber Fighters.
The attacks began in September last year, according to Radware, which specializes in commercial computer security and has been investigating the cyberassaults.
“The landscape we are seeing is essentially a persistent industry sector attack that is unprecedented,” Herberger said.
Attackers have shrewdly tailored requests to target encrypted pages or data, which are more complicated to process and therefore tax Web sites more, according to Radware.
Such requests are particularly nefarious because encrypted exchanges are often shielded from security software intended to guard against attacks.
Herberger described how hackers sometimes use DDoS attacks to trigger fail systems that can sometimes allow invaders to get to data.
“I call it the battering ram effect,” Herberger said. “They literally batter in the front door; that is a really dark side of this world.”
Attacks on banks could also be test runs for assaults on other business sectors or even smart systems controlling vital infrastructure.
“Let’s suppose this is state sponsored,” Herberger said. “Could these not be dry runs? If the banks are permeable what is the likelihood that other systems are?
John Bumgarner of the US Cyber Consequences Unit, a non-profit group that studies the impact of cyberthreats, cautioned against rushing to assign blame for the attacks.
“There is no irrefutable evidence that the Iranian government was responsible,” Bumgarner said.
Nearly half of China’s major cities are suffering “moderate to severe” levels of subsidence, putting millions of people at risk of flooding, especially as sea levels rise, according to a study of nationwide satellite data released yesterday. The authors of the paper, published by the journal Science, found that 45 percent of China’s urban land was sinking faster than 3mm per year, with 16 percent at more than 10mm per year, driven not only by declining water tables, but also the sheer weight of the built environment. With China’s urban population already in excess of 900 million people, “even a small portion
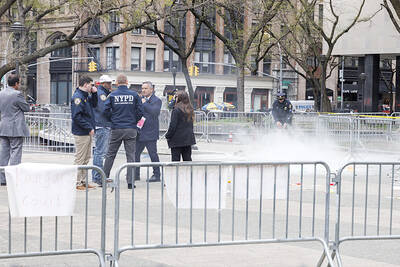
UNSETTLING IMAGES: The scene took place in front of TV crews covering the Trump trial, with a CNN anchor calling it an ‘emotional and unbelievably disturbing moment’ A man who doused himself in an accelerant and set himself on fire outside the courthouse where former US president Donald Trump is on trial has died, police said yesterday. The New York City Police Department (NYPD) said the man was declared dead by staff at an area hospital. The man was in Collect Pond Park at about 1:30pm on Friday when he took out pamphlets espousing conspiracy theories, tossed them around, then doused himself in an accelerant and set himself on fire, officials and witnesses said. A large number of police officers were nearby when it happened. Some officers and bystanders rushed

HYPOCRISY? The Chinese Ministry of Foreign Affairs yesterday asked whether Biden was talking about China or the US when he used the word ‘xenophobic’ US President Joe Biden on Wednesday called for a hike in steel tariffs on China, accusing Beijing of cheating as he spoke at a campaign event in Pennsylvania. Biden accused China of xenophobia, too, in a speech to union members in Pittsburgh. “They’re not competing, they’re cheating. They’re cheating and we’ve seen the damage here in America,” Biden said. Chinese steel companies “don’t need to worry about making a profit because the Chinese government is subsidizing them so heavily,” he said. Biden said he had called for the US Trade Representative to triple the tariff rates for Chinese steel and aluminum if Beijing was

Beijing is continuing to commit genocide and crimes against humanity against Uyghurs and other Muslim minorities in its western Xinjiang province, U.S. Secretary of State Antony Blinken said in a report published on Monday, ahead of his planned visit to China this week. The State Department’s annual human rights report, which documents abuses recorded all over the world during the previous calendar year, repeated language from previous years on the treatment of Muslims in Xinjiang, but the publication raises the issue ahead of delicate talks, including on the war in Ukraine and global trade, between the top U.S. diplomat and Chinese