If someone offered to build a house for you that was completely safe from burglars, you’d know they were either mistaken or lying.
It’s the same when it comes to adding protection to make your computer completely safe. It just can’t be done.
But that doesn’t — and shouldn’t — stop you from doing your best. It’s smart to do what you can, but remain aware you’re never totally out of danger.
All this has been on my mind because of news stories recently — among them one about Canadian researchers who found a giant network of Chinese hackers who had tapped into computers worldwide, including one owned by the Dalai Lama.
Then there’s the highly sophisticated Conficker worm that’s been in the news recently. Those threats were created by sophisticated computer criminals and can’t be stopped completely. But there are things you must do to protect your computer against those who are just as malicious but not quite as talented.
Firewall
That’s the No. 1 line of defense — the equivalent of a deadbolt on your front door. Starting with Windows XP and continuing with Vista, the free firewall supplied with Windows is actually pretty good.
Since it’s built into Windows, there is little chance it will interfere with the operation of your computer. Take a moment to make sure your firewall is turned on. If you don’t know how to go about that, just type the word “firewall” into your Windows search menu.
NAT
Those letters stand for Network Address Translation. If you want to know how it works, go to this Web address: tinyurl.com/ehmmh. All you really need to know is that NAT also provides security.
Luckily, computer routers usually have NAT protection built in. So if you have a computer network, you already have this added layer of protection that lets your computer hide behind the router.
Malware protection
I’m using the term malware because I want to include spyware, adware, viruses, worms and other stealthy threats used by hackers to take over your computer. I know it sounds basic, but you must use good programs to check for all these threats.
I’ve listed many of them in the past and don’t have the space to list the programs again. There are both good free and commercial programs.
Many readers, unwilling to go through the uncertainty and hassle of tracking down free programs, might be well-served to just pay the price for commercial protection from Symantec, McAfee or other providers. Check online reviews at cnet.com or pcworld.com for the best performers.
Once you add a program, keep it updated. Also regularly update Windows. As was true in the case of Conficker, Microsoft regularly issues patches to combat new threats.
One handy thing to know: If your anti-virus programs or Windows won’t update, that’s a sign that malware is active in your computer, blocking the update.
No software needed
One of the best defenses is common sense. Many threats are implanted in your computer from suspect Web pages. So avoid X-rated sites, hacker sites and Web sites that offer access to free versions of songs and commercial software.
Many sites offering free games are both well-done and amusing — along with being danger spots for adware and spyware.
Also be wary of e-mail attachments. Even a sender you know and trust could unknowingly send along something harmful. Ignore e-mails with attachments from people you don’t know.
Now the deadbolts are locked and the alarm system is on. But stay suspicious. The best computer protection is a savvy and skeptical user.

President William Lai (賴清德) yesterday delivered an address marking the first anniversary of his presidency. In the speech, Lai affirmed Taiwan’s global role in technology, trade and security. He announced economic and national security initiatives, and emphasized democratic values and cross-party cooperation. The following is the full text of his speech: Yesterday, outside of Beida Elementary School in New Taipei City’s Sanxia District (三峽), there was a major traffic accident that, sadly, claimed several lives and resulted in multiple injuries. The Executive Yuan immediately formed a task force, and last night I personally visited the victims in hospital. Central government agencies and the

Australia’s ABC last week published a piece on the recall campaign. The article emphasized the divisions in Taiwanese society and blamed the recall for worsening them. It quotes a supporter of the Taiwan People’s Party (TPP) as saying “I’m 43 years old, born and raised here, and I’ve never seen the country this divided in my entire life.” Apparently, as an adult, she slept through the post-election violence in 2000 and 2004 by the Chinese Nationalist Party (KMT), the veiled coup threats by the military when Chen Shui-bian (陳水扁) became president, the 2006 Red Shirt protests against him ginned up by
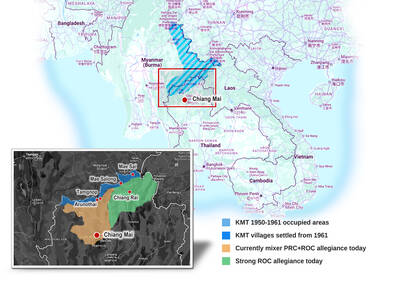
As with most of northern Thailand’s Chinese Nationalist Party (KMT) settlements, the village of Arunothai was only given a Thai name once the Thai government began in the 1970s to assert control over the border region and initiate a decades-long process of political integration. The village’s original name, bestowed by its Yunnanese founders when they first settled the valley in the late 1960s, was a Chinese name, Dagudi (大谷地), which literally translates as “a place for threshing rice.” At that time, these village founders did not know how permanent their settlement would be. Most of Arunothai’s first generation were soldiers

Among Thailand’s Chinese Nationalist Party (KMT) villages, a certain rivalry exists between Arunothai, the largest of these villages, and Mae Salong, which is currently the most prosperous. Historically, the rivalry stems from a split in KMT military factions in the early 1960s, which divided command and opium territories after Chiang Kai-shek (蔣介石) cut off open support in 1961 due to international pressure (see part two, “The KMT opium lords of the Golden Triangle,” on May 20). But today this rivalry manifests as a different kind of split, with Arunothai leading a pro-China faction and Mae Salong staunchly aligned to Taiwan.