For the last article in this American & British English series, we turn to a vocabulary set that evolved after America achieved independence from the UK, and as such has many differences: motor vehicle parts.
In American English, the fender frames the wheel well, preventing mud or rocks being thrown up by the rapidly turning tire. It is the source of the term “fender bender,” meaning a minor accident. In British English, the fender is called the “wing.”
In the UK, before cars were invented, one main form of transport was the horse-drawn carriage. The driver would store his boots in the “boot locker,” and over time this phrase would be shortened to the “boot.” In the US in the past, the main storage space was a trunk attached to the back of the car. Over time, storage space was integrated into the back of the car, and became known as the trunk. In British English, this space is called the “boot.”
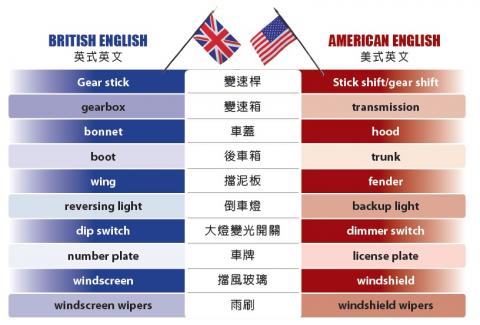
The metal part covering the engine is named after soft coverings for the head: “hood” in American English, from the Old English word hod, related to the Dutch hoed (hat), and “bonnet” in British English, from the Old French word bonet (cloth used as a headdress).
(Paul Cooper, Taipei Times)
在「美式英文與英式英文」的最後一個單元,我們要介紹一組詞彙:汽車零件。這些詞彙是在美國脫離英國獨立後演變而來的,因此有許多差異。
在美式英文中,「fender」(擋泥板)包住了輪艙(wheel well),防止快速旋轉的輪胎讓泥沙或石子飛濺出來。它是「fender bender」一詞的來源,表示擦撞、小車禍事故。英式英文則稱擋泥板為「wing」。
在英國,汽車尚未發明時的主要運輸工具是馬車。駕車的人將其靴子放在靴子櫃(boot locker)中,久而久之,該片語縮短為「boot」。過去美國的汽車,其主要置物空間是裝在車子後面的大行李箱(trunk)。後來,置物空間被整合到汽車的後部,並稱為「trunk」(後車箱)。英式英文則稱後車箱為「boot」。
金屬製的引擎蓋,其美式英文名稱卻是來自柔軟的衣物──風帽(hood),源於古英語字「hod」,與荷蘭文「hoed」(帽子)有關。引擎蓋在英式英文中稱為「bonnet」,源自古法語字「bonet」(用作頭巾的布)。
(台北時報林俐凱譯)

A: In its latest annual travel guide, Bloomberg recommended two restaurants in Taipei: Golden Pig barbeque from South Korea and two-Michelin-star restaurant A. B: Also, tourists should definitely try Taiwanese cuisine while they’re here. Mountain & Sea House, Shin Yeh Taiwanese Cuisine, and Fujin Tree Taiwanese Cuisine & Champagne are good options. A: For local snacks, Fu Hang Soy Milk, Fu-Ba-Wang Pigs’ Knuckles Restaurant, and Wang Ji Rice Dumplings are all very popular. B: And the gold medalists of the 2025 Taipei International Beef Noodle Festival — Yun Shui Kitchen, The Howard Plaza Hotel Taipei, and Come N’ Eat

A: Bloomberg just released its annual travel guide, titled “25 Best Places to Travel in 2026.” What were the best Asian destinations? B: There were actually six Asian hotspots: Taiwan’s Taipei, Malaysia’s Penang, Kazakhstan’s Almaty, Indonesia’s Rote Island, India’s Tiger Reserves, and Oman. A: With its mix of traditional food and modern cuisine, Taipei has become a rising food capital in Asia. B: As Bloomberg reported, “Taiwan is a place that bubbles up in culinary conversation because of its famed beverage, bubble tea, and its early adoption of modern night markets.” A: And Din Tai Fung has now

Facing relentless flooding and rising expenses, Dumble Farm in England has stopped selling milk and started an unexpected but therapeutic venture: cow cuddles. In 2022, the owners sold most of their dairy cows and began letting visitors spend time brushing, petting, and even hugging specially trained Highland cows for 95 pounds per session. This unusual shift reflects the rise of the so-called healing economy, a sector where animal-assisted experiences are marketed as emotional remedies for stress and burnout. While dogs and cats remain the most common therapy animals, cows are gaining popularity for their calm nature. At Dumble Farm, only cows that

Owls have long fascinated people with their distinctive appearance and mysterious habits. These nocturnal birds possess large, round eyes and a flat facial disc. Their feathers come in shades of brown, gray, or white, helping them blend easily into the darkness. The most remarkable trait of owls is that they can turn their heads without damaging blood vessels. Contrary to popular belief, they can only rotate their heads up to 270 degrees, not 360 degrees. Owls have 14 cervical vertebrae, which is twice as many as humans. This special physical structure compensates for their inability to move their eyes within their