Liberty Times (LT): What are your thoughts on the attempts by the US to block the spread of Huawei Technologies Co?
Li Jung-shian (李忠憲): The US-China trade war is ostensibly waged over trade deficits, but it is really about the structural changes that the US wants China to adopt.
China has reaped the benefits of free trade following its accession to the WTO. At the same time, it has kept its export subsidies, implemented regulations against foreign investors, used state-owned enterprises to monopolize the market and forced technology transfers from foreign firms, which it achieved by making the companies register in China, instead of allowing outright ownership. An end to the trade war is unlikely without addressing these issues.

Photo: Chang Chung-yi, Taipei Times
More than just a bid to control 5G technology, the US’ attempts to ban Huawei and ZTE Corp is part of a broader strategy of economic warfare against China.
Any modern state’s critical infrastructure would have to include a 5G telecommunications network, and the services the network provides would cover almost every facet of human activity. Therefore, the developer or operator of a 5G network would have great implications for national and information security.
Should the infrastructure, equipment or operation be compromised, a hostile party would be able to effectuate round-the-clock surveillance in the very least or cripple the entire network, which could plunge a nation into a crisis.
The US is a free and democratic state, while China is an authoritarian dictatorship — following Chinese President Xi Jinping’s (習近平) abrogation of term limits, power is being concentrated in even fewer hands.
China is assuredly not a free-market economy. Although the US helped China build its economy, it openly treats the US as its main potential adversary and maintains close ties with Russia and North Korea.
It has established a bloc via massive investments in Africa, and plies the Philippines with cash in the South China Sea, as well as Cambodia and Pakistan. Recently, it has taken to cultivating anti-US forces in Venezuela, practically the backyard of the US.
These signs point to China’s intention to confront the US across multiple theaters. In response, a bipartisan consensus to adopt a common strategy to counter China has formed in the US.
Taking the above into account, it is safe to say that US actions against Huawei and ZTE are not purely motivated by cybersecurity, but by national security as well. Considering the vital importance of 5G infrastructure, the US blockade of Huawei is an inevitable outcome.
LT: What are the security implications of using Huawei products for the government? What policies do you think the government should adopt?
Li: China is Taiwan’s main adversary. Xi has declared on multiple occasions that Beijing does not renounce the use of force against Taiwan.
Research has also demonstrated that Huawei cellphones contain a lot of mystery firmware, including hidden backdoors in complex systems. Without prior knowledge of a security issue that has already occurred, finding those backdoors would be like looking for a needle in a haystack.
If you find one cockroach in a house, you must assume more are in hiding — the same applies to cellphones.
Why is the use of Huawei smartphones banned at government offices? Because even assuming rigorous network security that shuts down suspicious connections made from within an intranet or through backdoors, those cellphones are still capable of collecting information while in the intranet and transmitting them to China after accessing an unregulated 4G environment.
The inherent characteristics of Internet technology allow diffused and multipurpose applications, enabling data transmission at different network layers.
Ensuring cybersecurity within the confines of an establishment does not protect information from being compromised; the use of Huawei devices itself must be regulated.
Cellphones are powerful in computing, storage, data speed and other applications. They are capable of forming a diffused source database. There are very few viable technical solutions to protect secrets that do not involve banning the devices. From a national security perspective, using telecommunication equipment manufactured by the enemy should be forbidden.
However, efforts to define peace and war are complicated by the unique conditions of Taiwan’s informational warfare environment and frustrates the government’s efforts to address problems.
The government should start by making an inventory of all communication devices that carry a Chinese brand or were manufactured in China. To install backdoors, China could utilize the design process of the former, while tempering the latter would have to take place in the manufacturing process. Therefore, the threat posed by devices carrying a Chinese brand is greater.
As perfect security does not exist, no cybersecurity measure can completely eliminate all security risks.
The government has to set clear priorities in managing potential risks, allocate resources according to those priorities and strictly enforce security regulations.
LT: Would the average user be affected if they use Huawei cellphones?
Li: The average user is mostly affected by the invasion of their privacy, including their location, photographs or videos and passwords for various applications, posing a threat to their finances and browsing history on social media or the Internet in general.
This is the kind of information that people usually keep private, even from their relatives. Is it any wonder that people would be distressed to find that such information has been flowing into an archive somewhere?
If there are backdoors programmed into Huawei cellphones, all information for mobile applications would be accessible and could be uploaded to Chinese databases as long as the cellphones have access to a 4G network, regardless of location or country.
As for how China targets users, it usually employs a hacking method called advanced persistent threat, which makes complex and multiple hacks against an individual or a group. The word “persistent” refers to the extraction of data over an extended period of time, which could be weeks, months or even years.
Any cellphone or device that has a built-in backdoor is infinitely easier to target and access. The Chinese state security agencies would know who you are, what your telephone number is, where you live and who is on your contact list. They would know your relationship to them, what they look at, who they had dinner with or what messages they sent on their cellphone.
With this information, they would know what kind of news story to best “suggest” to you, in which they would embed trojans.
I call on the people of Taiwan to distance themselves from Chinese-made cellphones or smart appliances. In the artificial intelligence age, information is more useful than money.
Regardless of type, smart appliances pose a significant information security risk to users. I have a friend who was recently elected to a position of significance and soon after, his wife won a lottery that presented them with a set of smart appliances as prize. As someone who is especially sensitive to information security issues, I feel that the win is creepy.
LT: Do you think the US’ containment of Huawei will succeed?
Li: I received my degree in Germany and I can tell you that Germany has a complicated relationship with the US, especially after Donald Trump became president. It could be said that Germany is one of the Western countries that is most friendly toward China.
At the same time, German TV channel Das Erste has been discussing the Huawei 5G network establishment issue, saying that 5G networks could affect the lives of people to the extent that the nation could be wiretapped or be subject to cyberwarfare.
Huawei has a decent grasp of technology and has invested a lot into 5G technology. However, it is nonetheless a Chinese company that relies strongly on the Chinese state.
The Chinese state is not a democratic government and has many regulations and laws in place that mandate companies to comply with the state’s intelligence gathering efforts. Therein lies the crux of the issue.
The US is indubitably the reigning champion in terms of international economy and military prowess, and shares with its European allies information about terrorist attacks. Should the US choose to withhold such information, it would lead to a great regression of US-German relations.
Whether the US’ containment of Huawei will be successful is a difficult question to answer, but it is evident that the US is aware of the inherent Chinese threat, and other nations, including Germany, should take note that at its core, China is an authoritarian country that does not observe human rights or democracy, nor the liberties guaranteed by them.
Translated by staff writers Jonathan Chin and Jake Chung

Nipah virus infection is to be officially listed as a category 5 notifiable infectious disease in Taiwan in March, while clinical treatment guidelines are being formulated, the Centers for Disease Control (CDC) said yesterday. With Nipah infections being reported in other countries and considering its relatively high fatality rate, the centers on Jan. 16 announced that it would be listed as a notifiable infectious disease to bolster the nation’s systematic early warning system and increase public awareness, the CDC said. Bangladesh reported four fatal cases last year in separate districts, with three linked to raw date palm sap consumption, CDC Epidemic Intelligence

The manufacture of the remaining 28 M1A2T Abrams tanks Taiwan purchased from the US has recently been completed, and they are expected to be delivered within the next one to two months, a source said yesterday. The Ministry of National Defense is arranging cargo ships to transport the tanks to Taiwan as soon as possible, said the source, who is familiar with the matter. The estimated arrival time ranges from late this month to early next month, the source said. The 28 Abrams tanks make up the third and final batch of a total of 108 tanks, valued at about NT$40.5 billion

Two Taiwanese prosecutors were questioned by Chinese security personnel at their hotel during a trip to China’s Henan Province this month, the Mainland Affairs Council (MAC) said yesterday. The officers had personal information on the prosecutors, including “when they were assigned to their posts, their work locations and job titles,” MAC Deputy Minister and spokesman Liang Wen-chieh (梁文傑) said. On top of asking about their agencies and positions, the officers also questioned the prosecutors about the Cross-Strait Joint Crime-Fighting and Judicial Mutual Assistance Agreement, a pact that serves as the framework for Taiwan-China cooperation on combating crime and providing judicial assistance, Liang
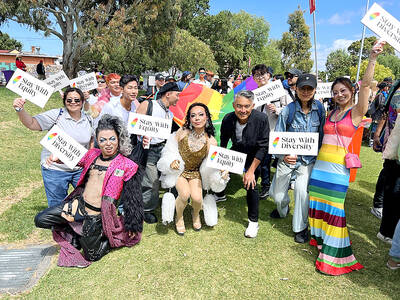
A group from the Taiwanese Designers in Australia association yesterday represented Taiwan at the Midsumma Pride March in Melbourne. The march, held in the St. Kilda suburb, is the city’s largest LGBTQIA+ parade and the flagship event of the annual Midsumma Festival. It attracted more than 45,000 spectators who supported the 400 groups and 10,000 marchers that participated this year, the association said. Taiwanese Designers said they organized a team to march for Taiwan this year, joining politicians, government agencies, professionals and community organizations in showing support for LGBTQIA+ people and diverse communities. As the first country in Asia to legalize same-sex